Using wireshark, let’s do some hands on practice of investigating internet / network trafic. Specifically investigating IPV4 and IPV 6 Header information.
I have run my wireshark Version 4.4.2 and immediately I was welcomed with a nice simple panel. The window was divided into two and the one below showd me some continuing heartbeat lines. This means there are activities in progress over some ports in my computer.
I wanted to investigate my wifi traffic. And I have opened detailed packet logs view by clicking over WIFI.
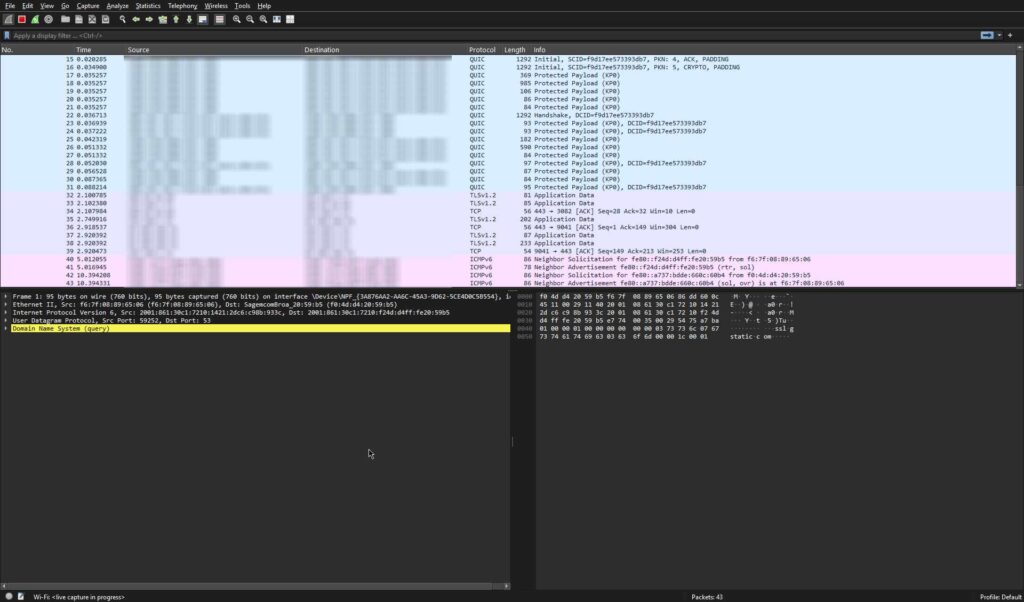
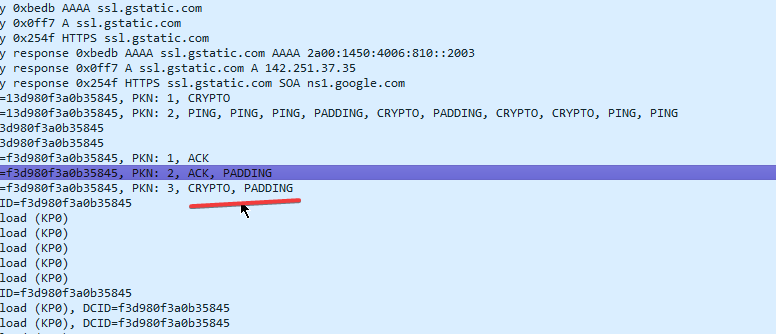
There is a little info title took my attention. Here it says CRYPTO, PADDING. And earlier and after this log there are more logs infos indicating some more crypto related messages. I am getting suspicious. I am not a crypto investor or miner. Is this related to anyhow an illegal crypto mining activity over my network or computer? who can tell what it is? I have to make a quick internet search about this info text on wireshark. If it is something really fishy, I will dig deeper.
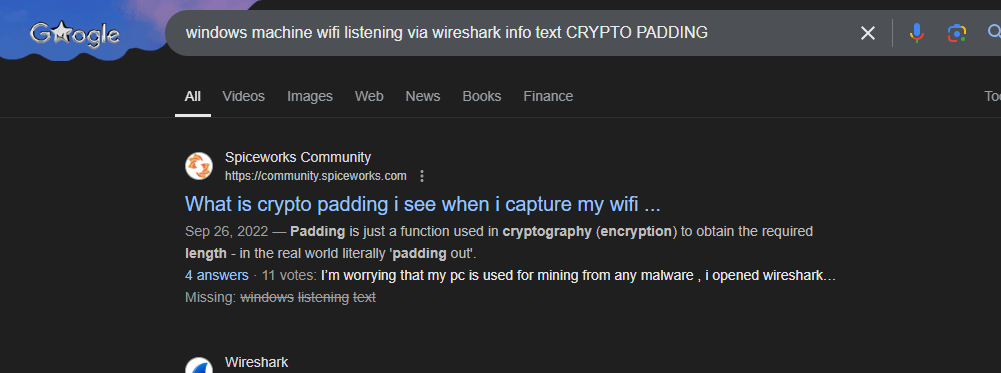
I have found a community discussion forum page talking about the same thing. And read through.
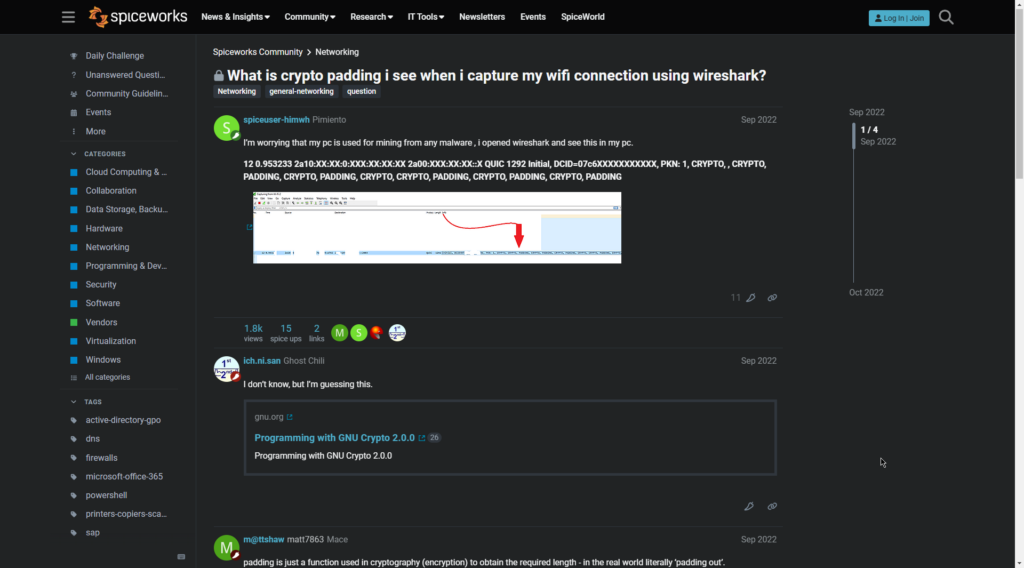
A user named ich.ni.sanGhost Chili fuesses it to be an open source cryptography standart program running on my computer. Gives a link for further investigation and went through this rabbot hole. It seemed legit to me. But I am not convinced yet. I have read through other opions from the community.
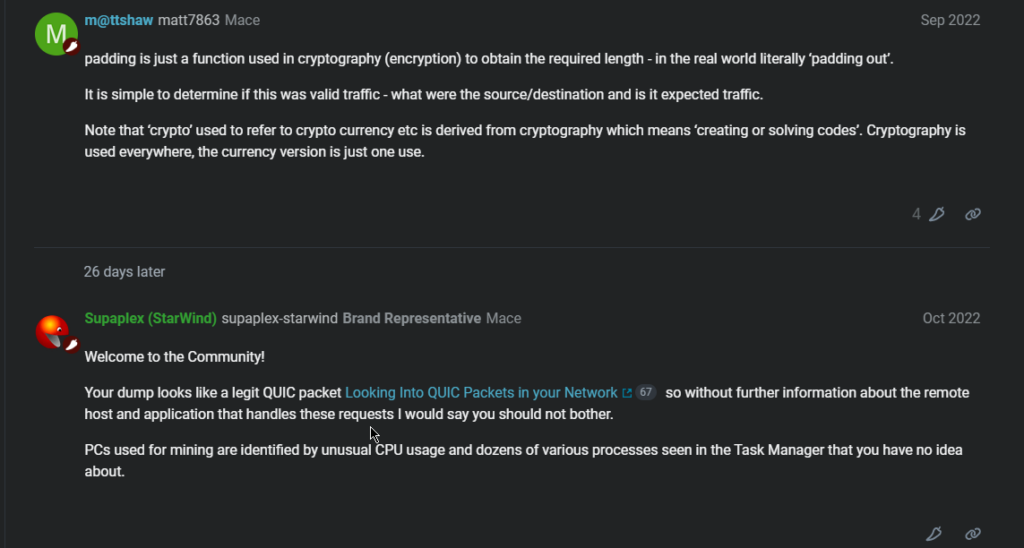
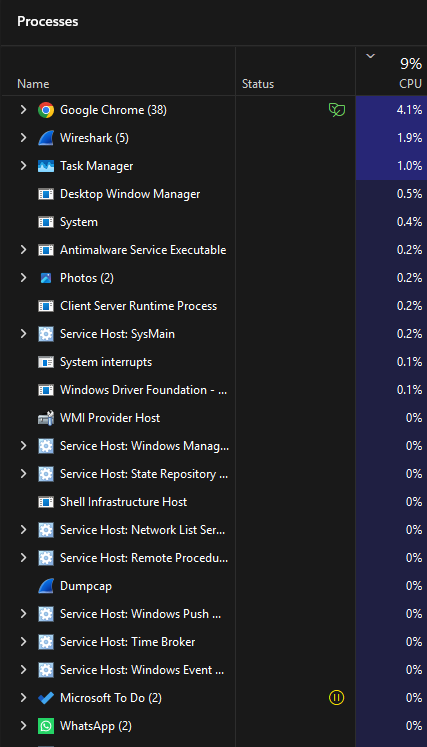
Another user named m@ttshawmatt7863Mace in the forum page gives even more detail with more convincing accent. Indicating that this is just a normal process of my computer. The Padding means a cryptography app is working in the backround but it is not neccessarity a crypto mining process but rather a security measurement of my own machine. He might be right but i need more evidence to support his claim. I read the following comment in the forum indicating that if thre was a Crypto mining activity on my machine, there should be a bif bump in my computer’s fan trying to cool, and upto dozens of unknown nonsense application running behind. I listened the fan on my computer, it was very quite despite I am still running wireshark behind. I have checked the taskes running behind on my computer and found nothing unusual and suspicious. Should I be releaved? or dig deeper.
When I looked backed into the wireshark screen, something interesting took my attention, the protocol used for transmision of this packet is named QUICK, it is not TCP or DNS. What does this protocols used for? I have not been iformed about all during my cyber security course program. But I know the basics. Lets do another quick google search on QUICK protocol.
It seems this is a new type of realy quick protocol that replaces TCP and TLS combination in the transport and session layers. I have read through an article well written by a researcher named Rakesh Seal. He explains that this protocol is widely used by FAANG companies, (Facebook, Apple, Amazon, Netflix and Google) for real fast streaming and data transfer over web. This is a new session layer protocol on top of UDP which replaces TLS/TCP. It offers reliability, security and speed thus regarded as new medium of transport layer protocol. QUICK packets are encrypted, so they are tamper proof from the middle interventions.
So, still nothing seems wrong about this packet. Should we leave it alone or investigate further? Let’s open the packet and see what’s more we can find out.